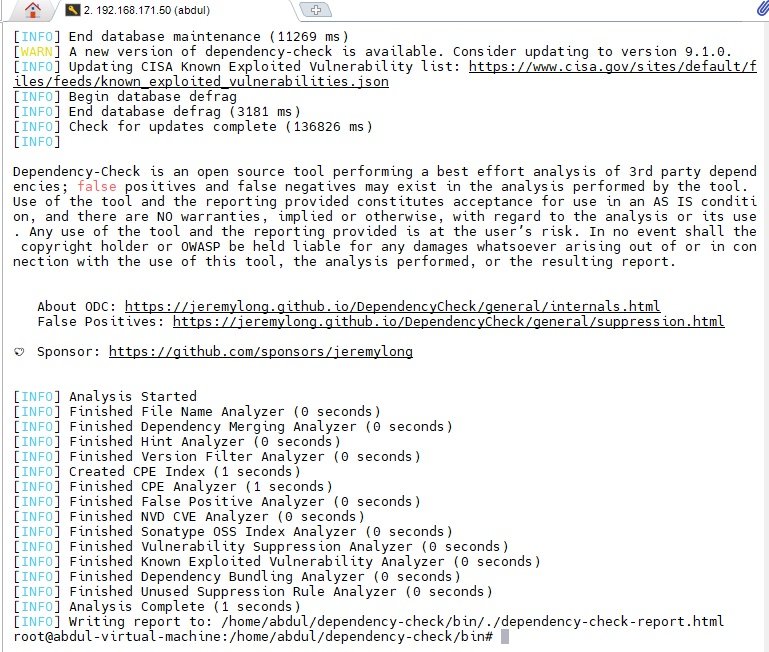
Intro SonarQube
- It is a static code analysis tool which perform code quality and code coverage of source code.
- It performs on source code where as OWASP-Dependency check performs on artifact/executable of application.
- Once the test cases has been performed then sonarqube uses its report to analys the code. In java project test cases report stored in jacoco (java code coverage), Nodejs uses istanbul.
Code Quality Check:
- In code quality check it finds bugs, vulnerability, codesmell, code duplication, technical debt in the soure code.
- Bugs: Errors in the code where application behave badly or piece of code does not work properly.
- Vulnerability: Weak section in the code which could be potential that outsider can hack or make it harm to application or source code.
- Codesmell: There could be potential issues in the future.
- code Duplication: repeated code has been written in the source code. Instead of writing identical code, developers can write function and use it in source code.
- Technical Debt: To fix the above issues, developers required time and it will be calcuated and produce the required time.
Code Coverage:
- When developers write code for test cases it checks the functionality of code. if there are X lines in the code and developers wrote 10 test cases to check the functionality which covers 80% of lines which meas code coverage is 80%, to achieve 100% developers need to write more test cases to cover the missing lines.
Versions: Two versions
- Community Edition: It is free of cost but have restriction where it can only perfrom master/main branch and fixed number of lines it can cover in source code. multiple branches and unrestricted code lines can be achieved by using developers edition or installing plugins in community edition.
- Developers Edition: It can perform on all branches and cover most source code lines as per package.
Package:
- Sonar Scanner: It is a tool which perform both code quality and code coverage. It will generate a report and will be uploaded to sonar server.
- Sonar Server: it will have report which sonar scanner generated.
Code
- code
- code
- code
code
- code
- code
- code
code
- code
- code
- code
Installation
Ubuntu
- Create 2 Ubuntu VMs, ,
- First vm install JDK, jenkins
- $sudo apt update
- $sudo apt install openjdk-17-jre-headless -y
- for jenkins installation: go to jenkins.ip/doc/book/installing/linux, copy the long term release command,
- create a script: open a file $vi jenkins.sh and paste the code. make this file executable $sudo chmod +x jenkins.sh , run the file ./jenkins.sh
- in browser http://ip:8080
- second vm install JDK, docker, sonarqube
- Docker Install: sonarqube installation can be done with various ways, create a docker container and install sonarqube using image.
- $sudo apt update
- $sudo apt install docker.io -y
- $docker pull hello-world (permission denied, by default only root user has permission to run docker commands, to give permission to other users enter the following command,
- Assing Permission to other user
- $sudo chmod 666 /var/run/docker.sock
- SonarQube Install: docker is installed, in order to create a docker container an image is required.
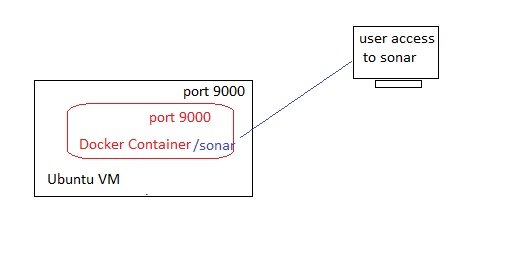
- $docker run -d --name sonar -p 9000:9000 sonarqube:lts-community (-d = run in detach mode, -p = port, 9000 entered twice, one for VM and one for container (docker is installed in a VM)
- To get the image of sonarqube go to hub.docker.com, official images and search sonarqube and take docker official image/tags and copy the link.
- sonarqube will be installed in a container, check container
- $docker container ls
- $docker exec -it container_ID /bin/bash (to go to container)
- Access Sonarqube:
- open browser http://ip:9000 (default user=admin, password =admin)
- Docker Install: sonarqube installation can be done with various ways, create a docker container and install sonarqube using image.
- Community Branch Plugin: sonarqube community edition have limitation, a developer has developed a plugin which will allow to run sonarqube without limitation, like running on all branches and no limit on code lines coverage.
- in google search : community branch plugin sonarqube or go to this url: https://github.com/mc1arke/sonarqube-community-branch-plugin?tab=readme-ov-file
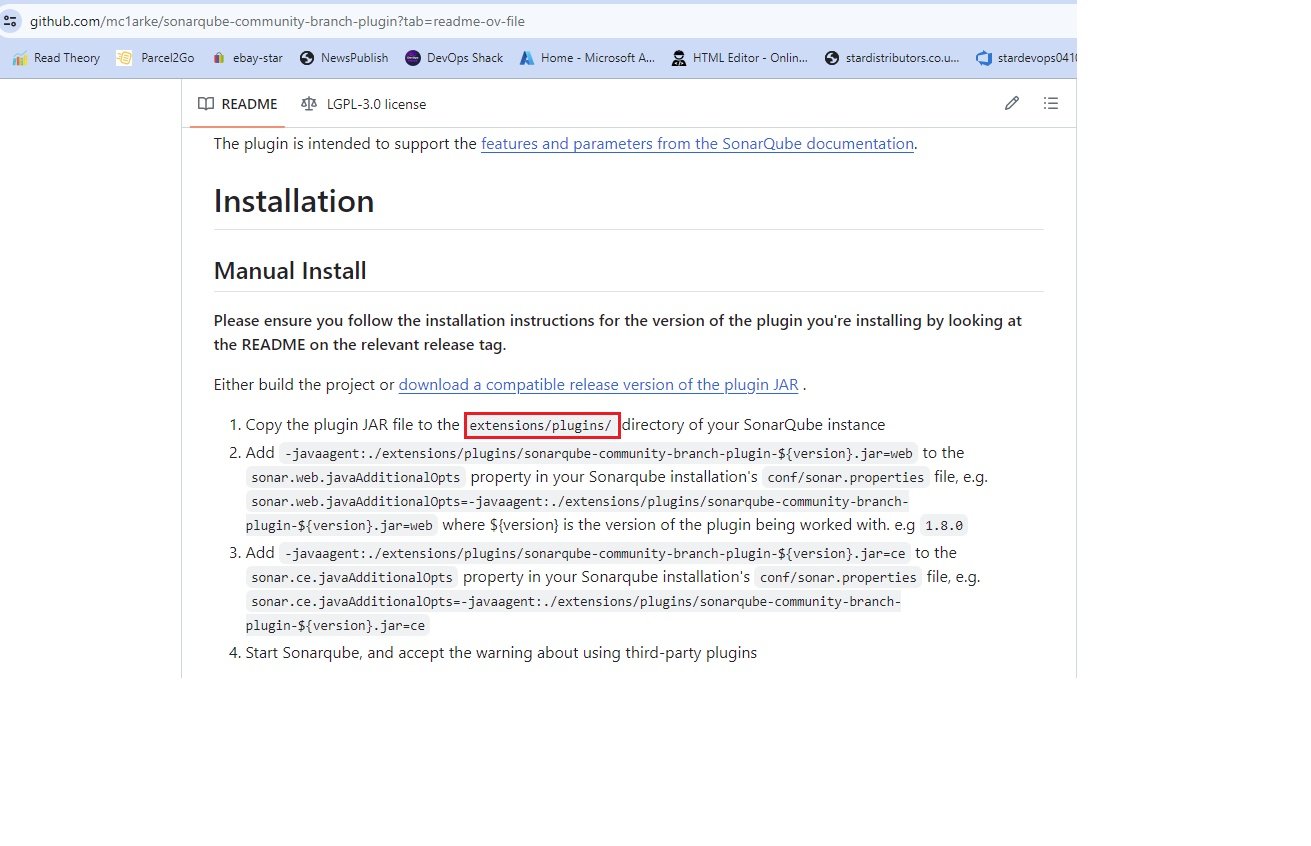
- Copy the plugin JAR file to the
extensions/plugins/directory of your SonarQube instance - Add
-javaagent:./extensions/plugins/sonarqube-community-branch-plugin-${version}.jar=webto thesonar.web.javaAdditionalOptsproperty in your Sonarqube installation'sconf/sonar.propertiesfile, e.g.sonar.web.javaAdditionalOpts=-javaagent:./extensions/plugins/sonarqube-community-branch-plugin-${version}.jar=webwhere ${version} is the version of the plugin being worked with. e.g1.8.0 - Add
-javaagent:./extensions/plugins/sonarqube-community-branch-plugin-${version}.jar=ceto thesonar.ce.javaAdditionalOptsproperty in your Sonarqube installation'sconf/sonar.propertiesfile, e.g.sonar.ce.javaAdditionalOpts=-javaagent:./extensions/plugins/sonarqube-community-branch-plugin-${version}.jar=ce - Start Sonarqube, and accept the warning about using third-party plugins
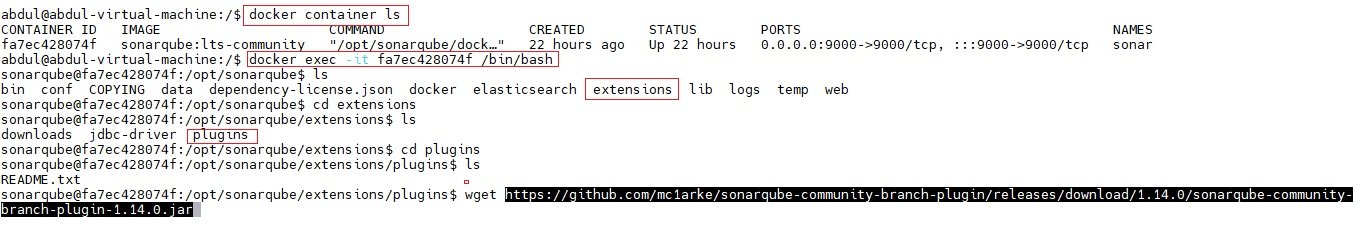
- copy .jar file and paste it in extensions/plugins folder
- To get the jar file click on releases in the right hand side of url and select version of sonarqube.

- right click and copy link address
- Go to docker and get into docker container
- $docker container ls (it will display container details)
- $docker exec -it container_ID /bin/bash
- $cd /extensions/plugins and download the jar file
- $wget paste the above copied link address.
- after downloaded, exit from container.
- $docker restart container_ID
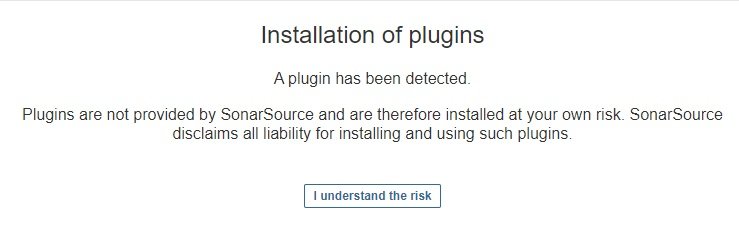
- go to sonarqube server/administration/marketplace / installed plugins
- or sonarqube with the above plugin can be installed by downloading docker image from the below repository.
- Docker image with the above plugin can be downloaded from repository: https://hub.docker.com/r/mc1arke/sonarqube-with-community-branch-plugin
- in google search : community branch plugin sonarqube or go to this url: https://github.com/mc1arke/sonarqube-community-branch-plugin?tab=readme-ov-file
Windows
- Download the Docker Desktop installer from the Docker website.
- Run the installer and follow the setup instructions.
AWS Linux
- code
- code
- code
Mac O/S
- Download Docker Desktop for Mac from the Docker website.
- Install Docker Desktop by dragging it to the Applications folder.
Install Docker
- $sudo apt install docker.io -y
- $docker pull hello-world
- $sudo chmod 666 /var/run/docker.sock (Assign permission to other users to access docker)
Install sonarqube in docker container
- $docker run -d --name sonarqube -p 9000:9000 sonarqube:lts-community
-d: Run the container in detached mode.--name sonarqube: Assign a name to the container (you can use any name).-p 9000:9000: port map 9000 for host and container (sonarqube installed in a container which is inside a host(docker).
- Access: http://localhost/ip:9000
- user: admin
- Password: admin
- $docker run -d --name sonarqube -p 9000:9000 sonarqube:lts-community
Install sonarqube with distribution Zip file
-
# SonarQube Installation
# Switch back to the ubuntu user
sudo -i# Install the 'unzip' package
apt install unzip# Add a new user named 'sonarqube'
adduser sonarqube# Switch to the 'sonarqube' user
sudo su sonarqube# Download SonarQube distribution zip file
wget https://binaries.sonarsource.com/Distribution/sonarqube/sonarqube-9.4.0.54424.zip# Unzip the downloaded file
unzip sonarqube-9.4.0.54424.zip# Set permissions for the SonarQube directory
chmod -R 755 /home/sonarqube/sonarqube-9.4.0.54424# Change ownership of the SonarQube directory
chown -R sonarqube:sonarqube /home/sonarqube/sonarqube-9.4.0.54424# Change to the SonarQube binary directory
cd sonarqube-9.4.0.54424/bin/linux-x86-64/# Start the SonarQube server
./sonar.sh start - code
- code
-
Integration with Jenkins
- After You setup Sonarqube then next install plugin sonar scanner plugin in jenkins and configure it in Manage Jenkins /Tools.
- SonarQube Scanner: select and install
- Eclipse Temurin Installer ( To keep different versions of tools)
- Configure sonar Scanner plugins
- Go to Manage Jenkins\Tools
- SonarScanner for MS Build Installations:It is used for MS Build Projects and for all other use sonar qube scanner installaiton.
- Sonar Qube Scanner Installation:
- Add installer:
- Name: sonar-scanner
- Version: latest
- Maven: configure if Maven is not installed in ubuntu
- Sonar Server Configuration
- Manage Jenkins /System /SonarQube Servers
- Add SonarQube
- Name = sonar
- Server URL = http://ip:9000
- Server Authentication token:
- Add
- Generate token:
- Go to sonarqube server URL\adinistration\security\user\ click on update tokens or you can go to manage jenkins\credentials
- Enter name = sonar-token, generate and copy token
- In add section enter the following:
- Domain: global credentials.
- Kind: secret text
- scope: (global, jenkins,nodes, items, all child items)
- secret : paste token
- ID: sonar-token
- DescriptionL sonar-token
- click add and select sonar-token.
- code
Configuration/Settings
Projects:
- From Azure Devops:
- From Bitbucket Server:
- From Bitbucket cloud:
- From Github:
- From Gitlab:
Issues:
- when perform code analysis, bugs, vulnerability etc will be displayed here.
Rules
- different rules are setup for every programming language.
- Group of rules for every language which is used to analyse code. copy and create custom rule.
- Here you can include/exclude any rule which is not needed to be analysed.
Quality Profiles
- rules of different language are available.
Quality Gates
- Here you can define the criteria of quality of code,
Administration:
- Configuration:
- General settings: smtp configuration,
- Authentication: github, gitlab, bigbucket
- Devops platform integration: Github, bigbucket, azure devops, Gitlab
- JaCoCo: It is defined code (in java: under <properties> xxxx </properties>, test case results are stored in jacoco.exec)
- Languages: java, ruby, python, list of suffixes.
- Encryption:
- Webhooks:
- General settings: smtp configuration,
- Security:
- Users: create new user, activate/deactivate, generate tokens.
- Groups:
- Sonar-Administrators: Administrator group
- Sonar-users: every authenticated user automatically belongs to this group.
- Global Permissions:
- Grant and revoke permissions to make changes at the global level.
- These permissions include editing Quality Profiles, executing analysis, and performing global system administration
- Permission Templates: create custom template.
- Projects:
- Management:
- Background task: When you run analysis, its status can be check here.
- System:
- current status: up/down,
- Detailed information of sonarqube.
- Download system information and logs.
- Marketplace:
- Version: current version installed and any available versions.
- Plugins:installed and new plugins can be install.
- Configuration:
Settings in POM.XML file:
Enable Code Coverage with JaCoCo, Add below items in POM.xml
- Before Writing Pipeline Make sure below content is added in your pom.xml to get the code coverage.
- <properties>
<!-- JaCoCo Properties -->
<jacoco.version>0.8.7</jacoco.version>
<sonar.java.coveragePlugin>jacoco</sonar.java.coveragePlugin>
<sonar.dynamicAnalysis>reuseReports</sonar.dynamicAnalysis>
<sonar.jacoco.reportPath>${project.basedir}/../target/jacoco.exec</sonar.jacoco.reportPath>
<sonar.language>java</sonar.language>
</properties> -
These properties are used to configure various aspects of the build process and the behavior of the tools involved, such as Java version, JaCoCo version (a code coverage tool), and SonarQube analysis settings.
Here's an explanation of each property:
<java.version>11</java.version>: Specifies that the project is configured to use Java version 11.
<jacoco.version>0.8.7</jacoco.version>: Specifies the version of the JaCoCo code coverage tool to be used in the project. In this case, version 0.8.7 is specified.
<sonar.java.coveragePlugin>jacoco</sonar.java.coveragePlugin>: Specifies that JaCoCo will be used as the coverage plugin for SonarQube. This means that JaCoCo will be responsible for generating code coverage reports that SonarQube will use for analysis.
<sonar.dynamicAnalysis>reuseReports</sonar.dynamicAnalysis>: Indicates that SonarQube should reuse existing reports generated during the build process, rather than performing its own dynamic analysis.
<sonar.jacoco.reportPath>${project.basedir}/../target/jacoco.exec</sonar.jacoco.reportPath>: Specifies the path to the JaCoCo coverage report file. This file is typically generated during the build process and contains information about code coverage.
<sonar.language>java</sonar.language>: Indicates that the project's primary language is Java. This is used by SonarQube to properly analyze the code.
-
<dependency> <groupId>org.jacoco</groupId> <artifactId>jacoco-maven-plugin</artifactId> <version>0.8.7</version> </dependency>
-
<plugin> <groupId>org.jacoco</groupId> <artifactId>jacoco-maven-plugin</artifactId> <version>${jacoco.version}</version> <executions> <execution> <id>jacoco-initialize</id> <goals> <goal>prepare-agent</goal> </goals> </execution> <execution> <id>jacoco-site</id> <phase>package</phase> <goals> <goal>report</goal> </goals> </execution> </executions> </plugin>
Sonar Analysis using Maven
- Step1: Set up Sonar Qube Server
- Install and set up a SonarQube server either locally or using a cloud-based solution like SonarCloud.
- Install Ubuntu, Install JDK, Install Docker, Install sonarqube in container using image.
- Step 2: Configure Sonarqube in Your Project.
- In your project's root directory, create or update the
pom.xmlfile to include the SonarQube plugin configuration. Add the following plugin to the<build>section: -
<plugins> <plugin> <groupId>org.sonarsource.scanner.maven</groupId> <artifactId>sonar-maven-plugin</artifactId> <version>3.9.0.2155</version> <!-- Replace with the latest version --> </plugin> </plugins>
- Define the SonarQube properties in your
pom.xmlto specify the SonarQube server URL, project key, project name, and project version. Add the following properties inside the<properties>section: -
<properties> <sonar.host.url>http://your-sonarqube-server-url</sonar.host.url> <sonar.projectKey>unique-project-key</sonar.projectKey> <sonar.projectName>Your Project Name</sonar.projectName> <sonar.projectVersion>1.0</sonar.projectVersion> </properties>
- In your project's root directory, create or update the
- Step 3: Generate SonarQube Token
- Log in to your SonarQube server.
- Navigate to "My Account" or "User Settings."
- Generate a new token for your analysis.
- Step 4: Integrate SonarQube Token.
- In your project's
pom.xml, add the SonarQube token as a property: -
<properties> <sonar.login>your-sonarqube-token</sonar.login> </properties>
- In your project's
- Step 5: Run the Analysis
- Open a terminal or command prompt.
- Navigate to your project's root directory.
- Run the following Maven command to perform the SonarQube analysis:
- mvn clean verify sonar:sonar
- The
cleanphase ensures a clean build. - The
verifyphase compiles and tests your code. - The
sonar:sonargoal triggers the SonarQube analysis.
- The
- Step 6: Review the Analysis Results.
- After the analysis is complete, open your web browser and navigate to your SonarQube server's URL.
- Log in to your SonarQube account.
- You will see your project listed with the analysis results, including code quality metrics, issues, and more.
- Step 7: Address Issues and Repeat.
- Review the issues and code quality metrics reported by SonarQube.
- Make necessary code changes to address the reported issues.
- Repeat the analysis steps to ensure improvements and monitor code quality over time.
- code
SonarQube for NodeJs
- To enable code coverage analysis for a Node.js-based application in SonarQube, you'll typically use a combination of tools to generate coverage reports and the SonarScanner to integrate those reports with SonarQube. Here are the general steps:
- Pre-Requisite:
-
Install SonarQube:
- Make sure you have SonarQube installed and running.
-
Install SonarScanner:
- Install the SonarScanner tool on your machine. You can find instructions in the official SonarScanner documentation.
-
Setup Node.js Project:
- Ensure your Node.js project uses a testing framework that supports coverage reporting, such as Mocha, Jest, or Istanbul.
-
- Step 1: Install Coverage Reporting Tool:
- Install a code coverage tool for your Node.js project. For example, you can use Istanbul, which is commonly used for this purpose. Install it as a development dependency:
- npm install --save-dev nyc
- Step 2: Run Tests with Coverage:
- Modify your test script in
package.jsonto include coverage. For example, if you're using Mocha and Istanbul, your script might look like this:-
"scripts": { "test": "nyc mocha" }
-
- Then, run your tests with coverage:
-
npm test
-
- Modify your test script in
- Step 3: Generate SonarQube Compatible Report:
- Convert the coverage report generated by your tool into a format compatible with SonarQube. For Istanbul, you can use the istanbul-sonarqube-instrumenter:
- npm install --save-dev istanbul-sonarqube-instrumenter
- After running your tests, use the instrumenter to generate the SonarQube-compatible report:
- nyc report --reporter=lcov
istanbul-sonarqube-instrumenter
- nyc report --reporter=lcov
- Convert the coverage report generated by your tool into a format compatible with SonarQube. For Istanbul, you can use the istanbul-sonarqube-instrumenter:
- Step 4: Run Sonar Scanner:
- Use the SonarScanner to analyze your project and send the coverage report to SonarQube. Modify your
sonar-project.propertiesfile accordingly:-
sonar.projectKey=my-project sonar.projectName=My Project sonar.sources=src sonar.tests=test sonar.javascript.lcov.reportPaths=coverage/lcov-report/*.lcov
-
- run Sonar Scanner:
- sonar-scanner
- Use the SonarScanner to analyze your project and send the coverage report to SonarQube. Modify your
- Step 5: View Results in SonarQube
- Open your SonarQube dashboard to view the analysis results, including code coverage metrics.
- code
SonarQube Arguments
- SonarQube provides a set of analysis parameters that you can use to configure and customize the behavior of the static code analysis. These parameters can be specified when running the analysis using the
sonar-scannercommand or when integrating SonarQube with your build tools. The available parameters may vary depending on the version of SonarQube and the analysis context. Below are some common SonarQube analysis parameters along with examples. - Project Configuration:
-Dsonar.projectKey: Unique identifier for your project.- sonar-scanner -Dsonar.projectKey=my-project
-Dsonar.projectName: Name of your project.-
sonar-scanner -Dsonar.projectName="My Project"
-
- Source Code and Language Settings:
-Dsonar.sources: Comma-separated list of directories containing source code.- sonar-scanner -Dsonar.sources=src
-Dsonar.language: Specify the main language of your project.- sonar-scanner -Dsonar.language=java
- Analysis Scope:
-Dsonar.inclusions/-Dsonar.exclusions: Include or exclude specific files from analysis.-
sonar-scanner -Dsonar.inclusions="src/**/*.java" -Dsonar.exclusions="src/test/**/*"
-
- SonarQube Server Configuration:
-Dsonar.host.url: URL of the SonarQube server.- sonar-scanner -Dsonar.host.url=http://localhost:9000
-Dsonar.login/-Dsonar.password: Authentication credentials for connecting to the SonarQube server.- sonar-scanner -Dsonar.login=myUsername -Dsonar.password=myPassword
- Quality Gate Configuration:
-Dsonar.qualitygate.wait: Wait for the SonarQube server to complete the analysis and return the quality gate status.- sonar-scanner -Dsonar.qualitygate.wait=true
- Project Version and Branch:
-Dsonar.projectVersion: Version of your project.- sonar-scanner -Dsonar.projectVersion=1.0
-Dsonar.branch.name: Specify the branch name if analyzing a specific branch.- sonar-scanner -Dsonar.branch.name=feature-branch
- Other Settings:
-Dsonar.links.scm: Specify the link to your source code management system.- sonar-scanner -Dsonar.links.scm=https://github.com/my-organization/my-project
-Dsonar.verbose: Output more detailed logs during the analysis.- sonar-scanner -Dsonar.verbose=true
Setting Up SonarQube with Jenkins Pipeline
- Step 1: Create a Ubuntu VM & install JDK, Docker
- $sudo apt update
- $sudo apt install openjdk-17-jre-headless -y
- $sudo apt install docker.io -y
- sudo chmod 666 /var/run/docker.sock (Assing permission to other users)
- Step 2: Setup SonarQube LTS-Community Version
- docker run -d --name sonar -p 9000:9000 sonarqube:lts-community
- For community branch plugin Version of SonarQube:
- docker run -d --name sonar -p 9000:9000 mc1arke/sonarqube-with-community-branch-plugin
- Step 3: Install SonarQube Scanner Plugin & Configure in Jenkins Tools:
- After You setup Sonarqube then next install plugin sonar scanner plugin in jenkins and configure it in Manage Jenkins /Tools.
- SonarQube Scanner: select and install
- Eclipse Temurin Installer ( To keep different versions of tools)
- Configure sonar Scanner plugins
- Go to Manage Jenkins\Tools
- SonarScanner for MS Build Installations:It is used for MS Build Projects and for all other use sonar qube scanner installaiton.
- Sonar Qube Scanner Installation:
- Add installer:
- Name: sonar-scanner
- Version: latest
- Maven: configure if Maven is not installed in ubuntu
- Sonar Server Configuration
- Manage Jenkins /System /SonarQube Servers
- Add SonarQube
- Name = sonar
- Server URL = http://ip:9000
- Server Authentication token:
- Add
- Generate token:
- Go to sonarqube server URL\adinistration\security\user\ click on update tokens or you can go to manage jenkins\credentials
- Enter name = sonar-token, generate and copy token
- In add section enter the following:
- Domain: global credentials.
- Kind: secret text
- scope: (global, jenkins,nodes, items, all child items)
- secret : paste token
- ID: sonar-token
- DescriptionL sonar-token
- click add and select sonar-token.
- Step 4: Configure Webhook in Sonar Qube
- Before adding a quality gate in the pipeline, ensure a webhook is added in SonarQube:
- Go to Administration > Configuration > Webhook.
- Add the following format:
JENKINS_URL/sonarqube-webhook/
- Before adding a quality gate in the pipeline, ensure a webhook is added in SonarQube:
- Step 5: Jenkins Pipeline
-
pipeline { agent any tools { maven 'maven3' jdk 'jdk17' sonar 'sonar-scanner' // Ensure SonarQube scanner tool is configured } environment { SCANNER_HOME= tool 'sonar-scanner' } stages { stage('Git Checkout') { steps { git 'https://github.com/jaiswaladi2468/BoardgameListingWebApp.git' } } stage('Compile') { steps { sh "mvn compile" } } stage('Test') { steps { sh "mvn test" } } stage('SonarQube Analysis') { steps { withSonarQubeEnv('sonar-1') { sh ''' $SCANNER_HOME/bin/sonar-scanner -Dsonar.projectName=Boardgame -Dsonar.projectKey=Boardgame \ -Dsonar.branch.name=pre-master -Dsonar.java.binaries=target/classes ''' } } } stage('Quality Gate Check') { steps { script { waitForQualityGate abortPipeline: false, credentialsId: 'new-sonar-token' } } } stage('Build') { steps { sh "mvn package" } } } }
-
- code
code
- code
- code
- code
code
- code
- code
- code
Project: Perform Code Analysis on BoardGameListingWebApp
Installation
- Create 2 VMs (ubuntu),
- first vm install JDK, jenkins
- $sudo apt update
- $sudo apt install openjdk-17-jre-headless -y
- for jenkins installation: go to jenkins.ip/doc/book/installing/linux, copy the long term release command,
- create a script: open a file $vi jenkins.sh and paste the code. make this file executable $sudo chmod +x jenkins.sh , run the file ./jenkins.sh
- in browser http://ip:8080
- second vm install JDK, docker
- sonarqube installation can be done with various ways, create a docker container
- $sudo apt update
- $sudo apt install docker.io -y
- $docker pull hello-world (permission denied, by default only root user has permission to run docker commands, to give permission to other users enter the following command,
- $sudo chmod 666 /var/run/docker.sock
- docker is installed, in order to create a docker container an image is required.
- $docker run -d --name sonar -p 9000:9000 sonarqube:lts-community (-d = run in detach mode, -p = port, 9000 entered twice, one for VM and one for container (docker is installed in a VM)
- To get the image of sonarqube go to hub.docker.com, official images and search sonarqube and take docker official image/tags and copy the link.
Install Plugins on Jenkins & Perform code analysis
- Authentication (username & token) and URL
- Required: Configure Sonarqube server to upload the result & Scanner to perform analysis:
- Manage Jenkins/Plugins/Available Plugins:
- SonarQube Scanner: select and install
- Eclipse Temurin Installer ( To keep different version of tools)
- Configure sonar Scanner plugins
- Go to Manage Jenkins\Tools
- SonarScanner for MS Build Installations:It is used for MS Build Projects and for all other use sonar qube scanner installaiton.
- Sonar Qube Scanner Installation:
- Add installer:
- Name: sonar-scanner
- Version: latest
- Maven: configure if Maven is not installed in ubuntu
- Sonar Server Configuration
- Manage Jenkins /System /SonarQube Servers
- Add SonarQube
- Name = sonar
- Server URL = http://ip:9000
- Server Authentication token:
- Add
- Generate token:
- Go to sonarqube server URL\adinistration\security\user\ click on update tokens or you can go to manage jenkins\credentials
- Enter name = sonar-token, generate and copy token
- In add section enter the following:
- Domain: global credentials.
- Kind: secret text
- scope: (global, jenkins,nodes, items, all child items)
- secret : paste token
- ID: sonar-token
- DescriptionL sonar-token
- click add and select sonar-token.
- Jenkins: create item (sonar-analysis)
- Name = sonar-analysis, select pipeline.
- Groovy Script: click here (make sure there are some case sensitive in code)
- click Build now
- Pipeline has been successfully executed.
- Check code Analysis in SonarQube Server:
Perform Code Analysis on BoardGameListingWebApp with Community Branch Plugin
- There are two ways: install community branch plugin on sonarqube server or use docker image with builtin community branch plugin.
- Create 2 VMs (ubuntu),
- first vm install JDK, jenkins
- $sudo apt update
- $sudo apt install openjdk-17-jre-headless -y
- for jenkins installation: go to jenkins.ip/doc/book/installing/linux, copy the long term release command,
- create a script: open a file $vi jenkins.sh and paste the code. make this file executable $sudo chmod +x jenkins.sh , run the file ./jenkins.sh
- in browser http://ip:8080
- second vm install JDK, docker, sonarqube
- sonarqube installation can be done with various ways, create a docker container
- $sudo apt update
- $sudo apt install docker.io -y
- $docker pull hello-world (permission denied, by default only root user has permission to run docker commands, to give permission to other users enter the following command,
- $sudo chmod 666 /var/run/docker.sock
- docker is installed, in order to create a docker container an image is required.
- $docker run -d --name sonar -p 9000:9000 sonarqube:lts-community (-d = run in detach mode, -p = port, 9000 entered twice, one for VM and one for container (docker is installed in a VM)
- To get the image of sonarqube go to hub.docker.com, official images and search sonarqube and take docker official image/tags and copy the link.

- sonarqube will be installed in a container, check container $docker container ls
- Access: open browser http://ip:9000 (default user=admin, password =admin)
- Plugin: sonarqube community edition have limitation, a developer has developed a plugin which will allow to run sonarqube without limitation, like running on all branches and no limit on code lines coverage.
- in google search : community branch plugin sonarqube or go to this url: https://github.com/mc1arke/sonarqube-community-branch-plugin?tab=readme-ov-file

- copy .jar file and paste it in extensions/plugins folder
- To get the jar file click on releases in the right hand side of url and select version of sonarqube.

- right click and copy link address
- Go to docker and get into docker container
- $docker container ls (it will display container details)
- $docker exec -it container_ID /bin/bash
- $cd /extensions/plugins and download the jar file
- $wget paste the above copied link address.
- sudo
- after downloaded, exit from container.
- $docker restart container_ID

- go to sonarqube server/administration/marketplace / installed plugins
- or sonarqube with the above plugin can be installed by downloading docker image from the below repository.
- Docker image with the above plugin can be downloaded from repository: https://hub.docker.com/r/mc1arke/sonarqube-with-community-branch-plugin
- $docker run -d --name sonar -p 9000:9000 mc1arke/sonarqube-with-community-branch-plugin
- in google search : community branch plugin sonarqube or go to this url: https://github.com/mc1arke/sonarqube-community-branch-plugin?tab=readme-ov-file
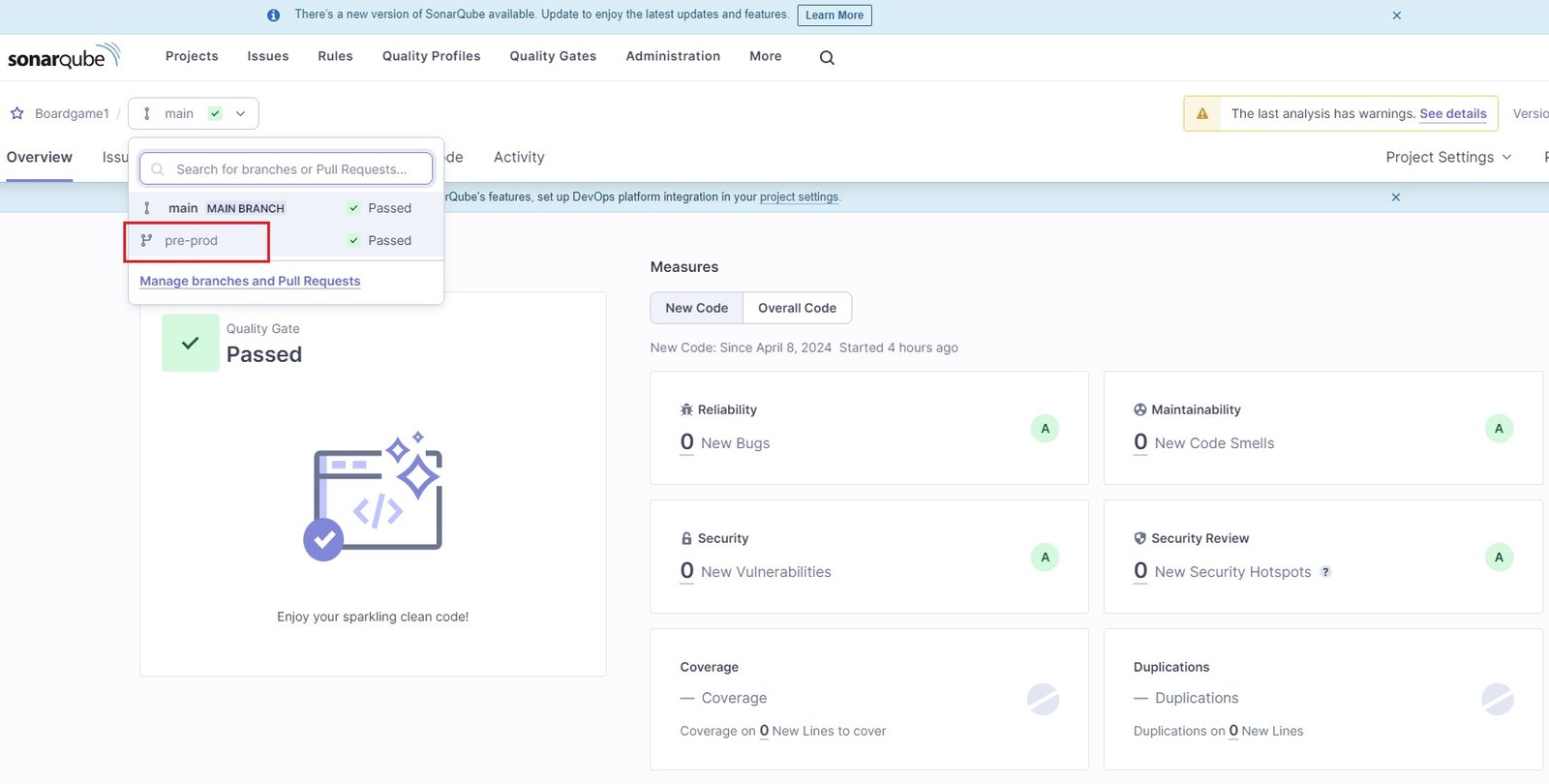
- Jenkins: create item (sonar-analysis-branch)
- Name = sonar-analysis, select pipeline.
- Groovy Script: click here (add this parameter for branch= -Dsonar.branch.name=pre-prod )
- click Build now
- Pipeline has been successfully executed on branch pre-prod.
- code
code
- code
- code
- code
code
- code
- code
- code
code
- code
- code
- code
code
- code
- code
- code
6
code
- code
- code
- code
code
- code
- code
- code
code
- code
- code
- code
code
- code
- code
- code
code
- code
- code
- code
code
- code
- code
- code
code
- code
- code
- code